DeepCTF Writeups
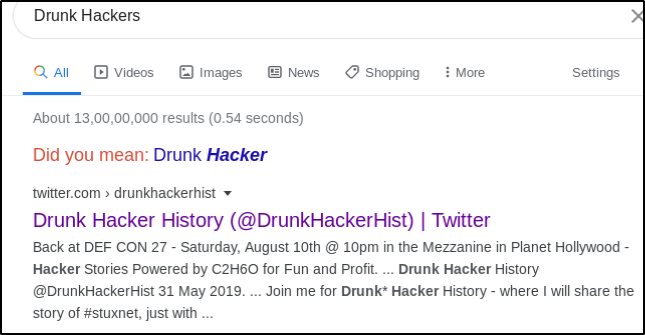
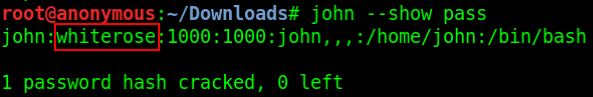
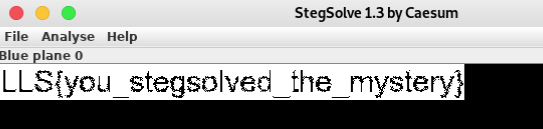
Hi everyone! I present you my writeup of the DeepCTF happened on April 4th, 2020. Let's Get Started---------------> OSINT Challenges: Challenge: History (80) DESCRIPTION- Where did it happen? 'Drunk Hackers' P.S. Hackers love that place Flag format - d33p{xxxxxx}] SOLUTION:: → Use commands - ⇒ Just search for Drunk Hackers on google ⇒ Open first link and we got the flag- → Flag - d33p{defcon} Challenge: SecXML (200) DESCRIPTION- <salesCommissions> <dollarAmount>FLAG</dollarAmount> </salesCommissions> The text file will help you get that information! Download file reach.txt SOLUTION:: → Use commands - ⇒ See the content of the file using command- cat reach.txt ⇒ Copy the above output, search it on google, some useful links will appear- ⇒ Open above links and search for " salesCommissions" text, you will get something like this- ⇒ Try out all the