DeepCTF Writeups
Hi everyone!
I present you my writeup of the DeepCTF happened on April 4th, 2020.
Let's Get Started--------------->
OSINT Challenges:
Challenge: History (80)
DESCRIPTION-Where did it happen?
'Drunk Hackers'
P.S. Hackers love that place
Flag format - d33p{xxxxxx}]
SOLUTION::
→ Use commands-
⇒ Just search for Drunk Hackers on google

⇒ Open first link and we got the flag-

→ Flag- d33p{defcon}
Challenge: SecXML (200)
DESCRIPTION-<salesCommissions>
<dollarAmount>FLAG</dollarAmount>
</salesCommissions>
Download file reach.txt
SOLUTION::
→ Use commands-
⇒ See the content of the file using command- cat reach.txt
⇒ Copy the above output, search it on google, some useful links will appear-

⇒ Open above links and search for "salesCommissions" text, you will get something like this-

⇒ Try out all the numbers in flag format and here, we got the flag from the second link
→ Flag- d33p{4016750}
J.T. Palladino used to be an intern in some company between June 2016 - August 2016
What is the zip code of the place he used to work?
Flag format: d33p{xxxxx}
SOLUTION::
→ Use commands-
⇒ See the LinkedIn profile of the above person
⇒ He is interned in Johnson & Johnson in Raritan, NJ location

⇒ Search the zip code of Raritan, NJ on google-
⇒ Zip code is 08869 and it the flag
→ Flag- d33p{08869}

⇒ From the description of the challenge and above output, we can understand this text is in Brainfuck language
⇒ Using website https://www.dcode.fr/brainfuck-language to decode the above text-
⇒ Here, we can see e=0x10001 is in hexadecimal, so we can convert it to decimal using website- https://www.rapidtables.com/convert/number/hex-to-decimal.html, we got e=65537
→ Flag- d33p{w3lc0m3_t0_d33pctf0x01!!!!!!!}

⇒ Open above links and search for "salesCommissions" text, you will get something like this-

⇒ Try out all the numbers in flag format and here, we got the flag from the second link
→ Flag- d33p{4016750}
Challenge: Life (200)
DESCRIPTION-J.T. Palladino used to be an intern in some company between June 2016 - August 2016
What is the zip code of the place he used to work?
Flag format: d33p{xxxxx}
SOLUTION::
→ Use commands-
⇒ See the LinkedIn profile of the above person
⇒ He is interned in Johnson & Johnson in Raritan, NJ location

⇒ Search the zip code of Raritan, NJ on google-
⇒ Zip code is 08869 and it the flag
→ Flag- d33p{08869}
Crypto Challenges:
Challenge: WTf`ish (70)
DESCRIPTION-
I Worked Worked Worked, Now My Brain Is F.....
Download file ciph3rt3xt.txt
Download file ciph3rt3xt.txt
SOLUTION::
→ Use commands-
⇒ See the content of the file using command- cat ciph3rt3xt.txt
→ Use commands-
⇒ See the content of the file using command- cat ciph3rt3xt.txt
⇒ From the description of the challenge and above output, we can understand this text is in Brainfuck language
⇒ Using website https://www.dcode.fr/brainfuck-language to decode the above text-

→ Flag- d33p{What_The_BrainF###}
Challenge: RSA 1.0 (150)
DESCRIPTION-
As Expected, Here You Have Your RSA Challenge... Enjoy :)
Download file param.txt
Download file param.txt
SOLUTION::
→ Use commands-
⇒ See the content of the file using command- cat param.txt
→ Use commands-
⇒ See the content of the file using command- cat param.txt
⇒ Here, we can see e=0x10001 is in hexadecimal, so we can convert it to decimal using website- https://www.rapidtables.com/convert/number/hex-to-decimal.html, we got e=65537
⇒ Install RsaCtfTool.py script if not have already, from https://github.com/Ganapati/RsaCtfTool using commands
git clone https://github.com/Ganapati/RsaCtfTool.git
cd RsaCtfTool
sudo apt install libgmp3-dev libmpc-dev
python3 -m venv .
. bin/activate
pip install -r "requirements.txt"
./RsaCtfTool.py
→ Also install following module otherwise you may get error, using following commands-
sudo apt install libmpc-dev
sudo apt install python3-pip
pip3 install --user gmpy2==2.1.0a2
git clone https://github.com/Ganapati/RsaCtfTool.git
cd RsaCtfTool
sudo apt install libgmp3-dev libmpc-dev
python3 -m venv .
. bin/activate
pip install -r "requirements.txt"
./RsaCtfTool.py
→ Also install following module otherwise you may get error, using following commands-
sudo apt install libmpc-dev
sudo apt install python3-pip
pip3 install --user gmpy2==2.1.0a2
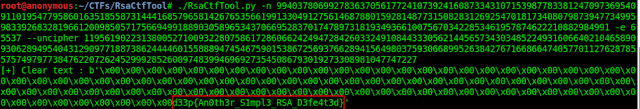
⇒ Now, using RsaCtfTool.py tool for decryption-
./RsaCtfTool.py -n 99403780699278363705617724107392416087334310715398778338124709736954091101954779586016351855873144416857965814267653566199133049127561468788015928148773150828312692547018173408079873947734995983392683281966120098505717566949918890305896534370669528370174789731819349366100756703422853461957874622210882984991 -e 65537 --uncipher 11956190223138005271009322807586172860662424947284260332491084433305621445657343034852249316066402104658909306289495404312909771887386244446015588894745467590153867256937662894156498037593066899526384276716686647405770112762878557574979773847622072624529992852600974839946969273545086793019273308981047747227
./RsaCtfTool.py -n 99403780699278363705617724107392416087334310715398778338124709736954091101954779586016351855873144416857965814267653566199133049127561468788015928148773150828312692547018173408079873947734995983392683281966120098505717566949918890305896534370669528370174789731819349366100756703422853461957874622210882984991 -e 65537 --uncipher 11956190223138005271009322807586172860662424947284260332491084433305621445657343034852249316066402104658909306289495404312909771887386244446015588894745467590153867256937662894156498037593066899526384276716686647405770112762878557574979773847622072624529992852600974839946969273545086793019273308981047747227
→ Flag- d33p{An0th3r_S1mpl3_RSA_D3fe4t3d}
Misc Challenges:
Challenge: Welcome (1)
DESCRIPTION-
Fill out our form!
https://forms.gle/HWAySjsUepwXF9mU6
https://forms.gle/HWAySjsUepwXF9mU6
SOLUTION::
⇒ You can also get the flag while filling the form, see the source code
→ Flag- d33p{w3lc0m3_t0_d33pctf0x01!!!!!!!}
Challenge: Let's chat! (35)
DESCRIPTION-
SOLUTION::
⇒ Just join the discord server using the above link, you will get the flag in the announcements section
→ Flag- d33p{disc0rd_r0cks}
→ Flag- d33p{disc0rd_r0cks}
Challenge: Exploity Things (50)
DESCRIPTION-
Which CVE affects the Cacti 1.2.8?
SOLUTION::
⇒ Just search on google for "Cacti 1.2.8 cve id"-

⇒ Open the third link-

→ Flag- d33p{CVE-2020-8813}
⇒ Just search on google for "Cacti 1.2.8 cve id"-

⇒ Open the third link-

→ Flag- d33p{CVE-2020-8813}
Challenge: Old stuff (50)
DESCRIPTION-
Turn the pages in a reversed way, I am one of the oldest ways, If you have anything confidential to say, Use me to change its way.
Flag format: d33p{answer}
Flag format: d33p{answer}
SOLUTION::
⇒ As we know caesar cipher is one of the oldest cipher, so it is itself the flag
→ Flag- d33p{caesar}
⇒ As we know caesar cipher is one of the oldest cipher, so it is itself the flag
→ Flag- d33p{caesar}
Forensic Challenges:
Challenge: WarmUp (50)
DESCRIPTION-
Warmup is necessary for long run. Here you go.
Download file note.jpg
Download file note.jpg
SOLUTION::
→ Use command-
⇒ When we get an image in CTF, we should first check strings behind it, use the command- strings note.jpg and the end we got the flag

→ Flag- d33p{Alw4y5_ch3ck_5tr1ng5}
→ Use command-
⇒ When we get an image in CTF, we should first check strings behind it, use the command- strings note.jpg and the end we got the flag

→ Flag- d33p{Alw4y5_ch3ck_5tr1ng5}
Challenge: MindYou (90)
DESCRIPTION-
What's In Your Mind?
Download file fsociety.zip
Download file fsociety.zip
SOLUTION::
→ Use commands-
⇒ Unzip the above zip file using command- unzip fsociety.zip, we got a png file mrrobot.png
⇒ On opening above png file, we see that it is corrupted because the header of the png image is not correct, so we will use the command to open the hex data of the image- hexeditor mrrobot.png to fix the magic number (89 50 4E 47) of above png image
⇒ Now, see the image and we got the flag-

→ Flag- d33p{M1nd_Y0ur_h34d3r5}
→ Use commands-
⇒ Unzip the above zip file using command- unzip fsociety.zip, we got a png file mrrobot.png
⇒ On opening above png file, we see that it is corrupted because the header of the png image is not correct, so we will use the command to open the hex data of the image- hexeditor mrrobot.png to fix the magic number (89 50 4E 47) of above png image
⇒ Now, see the image and we got the flag-
→ Flag- d33p{M1nd_Y0ur_h34d3r5}







Comments
Post a Comment